Data classification tags data according to its type, sensitivity, and value to the organization if altered, stolen, or destroyed. It helps an organization understand the value of its data, determine whether the data is at risk, and implement controls to mitigate risks. Data classification also helps an organization comply with relevant industry-specific regulatory mandates such as SOX, HIPAA, PCI DSS, and GDPR.
Data is classified according to its sensitivity level—high, medium, or low.

Since the high, medium, and low labels are somewhat generic, a best practice is to use labels for each sensitivity level that make sense for your organization. Two widely-used models are shown below.
| SENSITIVITY | MODEL 1 | MODEL 2 |
| High | Confidential | Restricted |
| Medium | Internal Use Only | Sensitive |
| Low | Public | Unrestricted |
If a database, file, or other data resource includes data that can be classified at two different levels, it’s best to classify all the data at the higher level.
Data classification can be performed based on content, context, or user selections:
Two additional dimensions of data classifications are:
Classifying data requires knowing the location, volume, and context of data. Most modern businesses store large volumes of data, which may be spread across multiple repositories:
Before you can perform data classification, you must perform accurate and comprehensive data discovery. Automated tools can help discover sensitive data at large scale. See our article on Data Discovery for more information.
Data classification must comply with relevant regulatory and industry-specific mandates, which may require classification of different data attributes. For example, the Cloud Security Alliance (CSA) requires that data and data objects must include data type, jurisdiction of origin and domicile, context, legal constraints, sensitivity, etc. PCI DSS does not require origin or domicile tags.
A data classification policy defines who is responsible for data classification—typically by defining Program Area Designees (PAD) who are responsible for classifying data for different programs or organizational units.
The data classification policy should consider the following questions:
Data classification can be the responsibility of the information creators, subject matter experts, or those responsible for the correctness of the data.
The policy also determines the data classification process: how often data classification should take place, for which data, which type of data classification is suitable for different types of data, and what technical means should be used to classify data. The data classification policy is part of the overall information security policy, which specifies how to protect sensitive data.
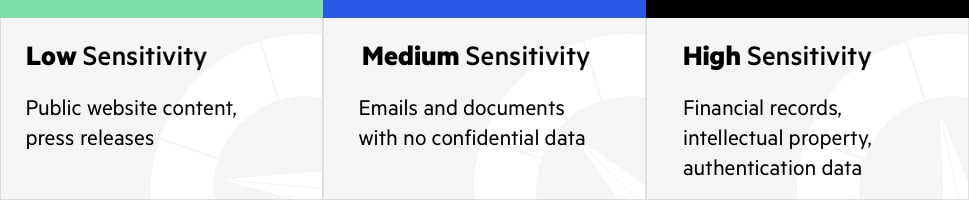
Following are common examples of data that may be classified into each sensitivity level.
| Sensitivity Level | Examples |
| High | Credit card numbers (PCI) or other financial account numbers, customer personal data, FISMA protected information, privileged credentials for IT systems, protected health information (HIPAA), Social Security numbers, intellectual property, employee records. |
| Medium | Supplier contracts, IT service management information, student education records (FERPA), telecommunication systems information, internal correspondence not including confidential data. |
| Low | Content of public websites, press releases, marketing materials, employee directory. |
See how Imperva Data Security Solutions can help you with data classification.
Imperva provides automated data discovery and classification, which reveals the location, volume, and context of data on premises and in the cloud.
In addition to data classification, Imperva protects your data wherever it lives—on premises, in the cloud and in hybrid environments. It also provides security and IT teams with full visibility into how the data is being accessed, used, and moved around the organization.
Our comprehensive approach relies on multiple layers of protection, including: